Home » IT security in transport and logistics: if you’re not careful, you could lose out

❯ The risk of becoming a victim of cybercrime is currently particularly high for the transport industry.
❯ At the same time, the majority of transport and logistics companies massively underestimate the risk.
❯ There are numerous reasons for this negligence, but the potential consequences can quickly threaten the survival of the company.
❯ Let DAKO show you how you can securely archive and manage your important data.
In its latest status report, the German Federal Ministry for Information Security (BSI) concludes that “the threat in cyberspace […] is higher than ever before.” The reasons for this are the greater threat posed by politically motivated attacks in the context of the war in Ukraine and the increasing differentiation of a ‘cybercriminal shadow economy’, which is able to carry out complex campaigns against entire branches of industry or infrastructure through coordinated attacks and the use of artificial intelligence. The idea of the lone hacker in a hoodie may be a Hollywood film icon, but the reality is often more complex.
The reason for the threat status in the transport and logistics industry lies in its strong influence on the operation of all other economic sectors and the correspondingly high potential for extortion. If the industry is disrupted, there is a risk of entire supply chains collapsing and a high level of damage to the economy as a whole. According to a survey by IT specialist insurer Hiscox, the transport industry is one of the five sectors of the economy most at risk. As early as 2021, 45% of the companies surveyed across Europe as part of this study reported having been victims of cyberattacks.
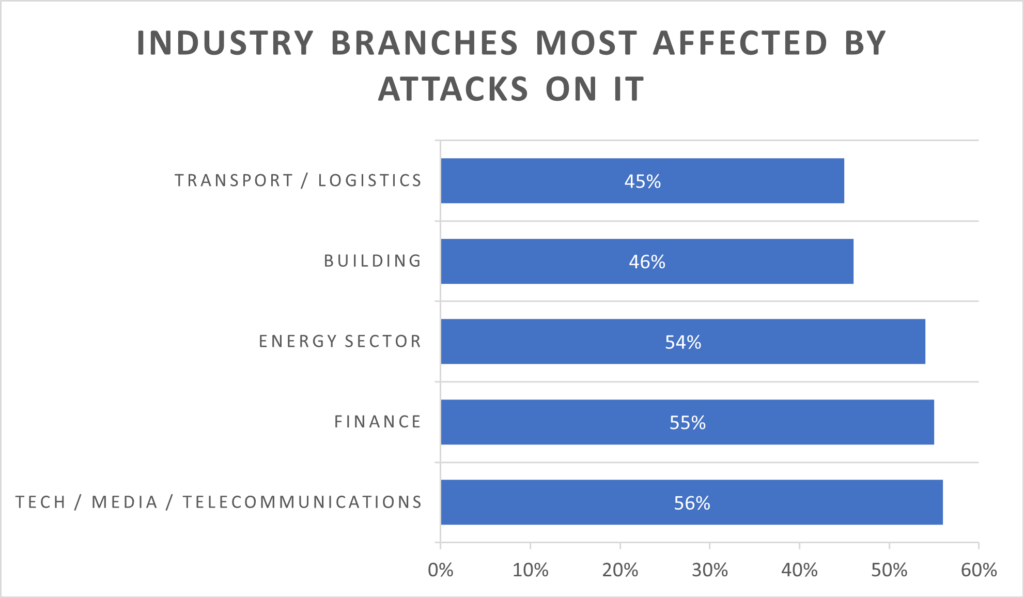
Source: https://www.gdv.de/gdv/medien/medieninformationen/it-sicherheit-in-handel-und-logistik-hohe-verwundbarkeit-geringes-problembewusstsein–131658
While insurers and IT experts are sounding the alarm, awareness of the problem among potentially affected companies still appears to be very low. The reasons for this were analysed in a representative Forsa survey last year: 84% of the companies surveyed believed that their IT systems were comprehensively protected. Around 70% assumed that their company was too small to be targeted by hackers, while a further 59% of respondents believed that their data was simply not of interest to criminals.
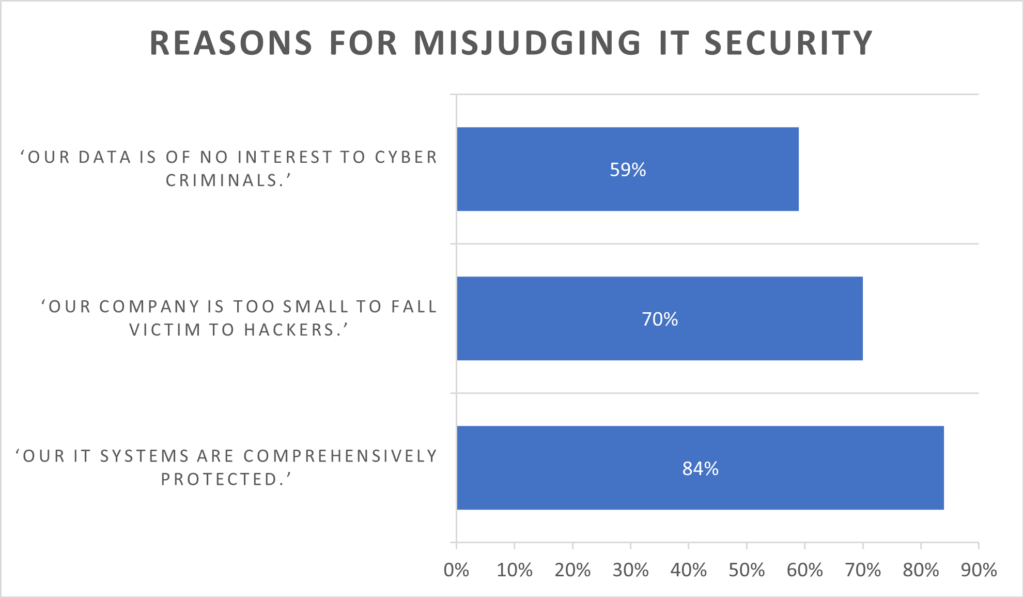
https://www.gdv.de/gdv/medien/medieninformationen/it-sicherheit-in-handel-und-logistik-hohe-verwundbarkeit-geringes-problembewusstsein–131658
It is easy to prove that these self-assessments are far removed from reality. A security check carried out on behalf of the German Insurance Association (GDV) on a sample of medium-sized companies from the retail and logistics / transport sectors revealed considerable weaknesses in 95% of the companies analysed, “which hackers could use to manipulate data or take over IT systems.”
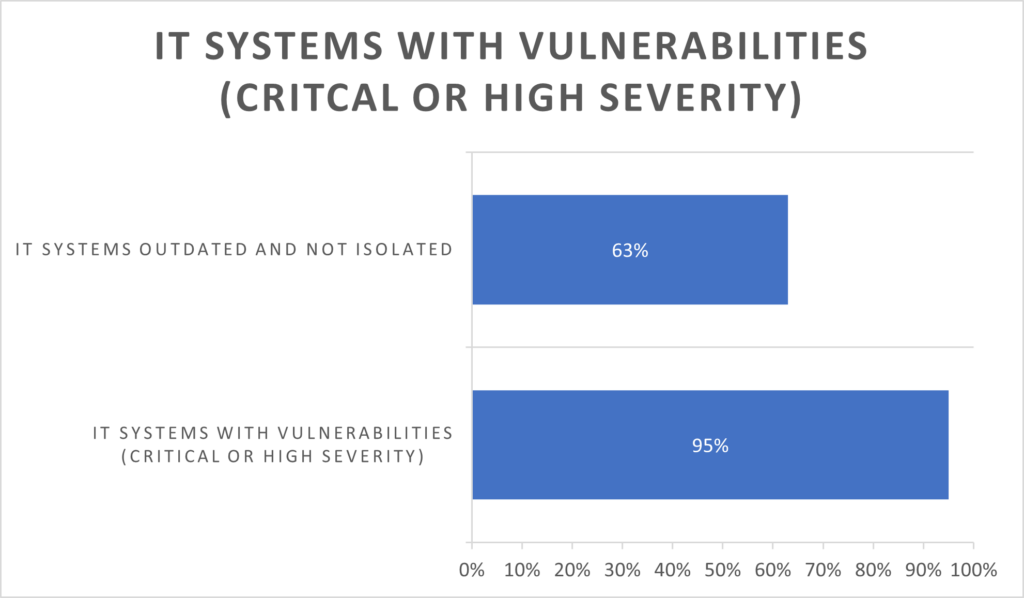
https://www.hiscox.de/cyber-readiness-report-2021/
In addition to the realisation that the existing IT landscape is inadequately secured in the majority of the companies surveyed, experts assume that small and medium-sized companies in particular are increasingly becoming targets of cyber criminals. The explanation for this is as simple as it is obvious: according to the BSI, attackers are taking the path of least resistance and attack where they can expect inadequate expertise and security precautions. Small and medium-sized transport companies often have neither the time nor the financial resources to regularly train their entire staff, hire IT experts, or outsource these sensitive tasks to external service providers. Highly networked business processes along the supply chain mean that attacks on smaller subcontractors often open up the digital gateways (so-called attack vectors) to larger players in the industry as well. In many cases, they don’t even need to attack these industry giants directly.
One of the reasons for misjudgements when it comes to IT security is that the massive consequences for a company’s own business are not realistically assessed. So, what happens when security gaps are exploited?
Transport companies can be affected by attacks on their IT in several ways. Like almost every other company, enterprises in this sector also manage data from customers and partners, as well as internal company data that is required for the processing and smooth functioning of day-to-day operations. Typically, this includes contact and delivery data, data on operational processes, balance sheet data, etc. If these are lost due to a cyber-attack, digital workflows are blocked. In the worst-case scenario, partners and customers may even become targets of fraud and blackmail attacks due to their own negligence. In addition to significant disruptions to regular operations and loss of sales, there is also the threat of loss of trust, delays in the supply chain or even fines for possible breach of contract. In addition, high fines can be levied under the European General Data Protection Regulation (GDPR) if customer data is leaked.
In addition to this threat scenario, transport companies are potentially focusing on a second pool of data, where blocked access or even complete loss can escalate into a business-threatening crisis: Fleet and driver-related data from tachographs, driver cards, working hours and expense calculations or the documentation of driving licence and vehicle checks. This data is not only irreplaceable for the day-to-day operation of a lorry fleet; it is also data that must be documented and securely archived by law.
If, for example, driving times and rest periods cannot be fully documented, the responsible Federal Office for Logistics and Mobility (BALM) may impose a fine of €750 per driver each day for which no evidence can be provided. Depending on the size of the fleet, an already tense situation can quickly turn into a business-threatening incident. In addition, there are the high costs and time required to restore all relevant systems, serious disruptions to operations, loss of trust among customers, partners and employees, and the possible misuse of employee data.
With all this in mind, it is clear that transport companies are not only exposed to a high threat potential for cybercrime – they also feel the consequences of such an incident particularly severely.
“I’m the only one using this PC. I’ve secured it with a password, and that’ll do it!” Another misconception about data security may sound something like this. However, the assumption that there is no risk of unauthorised access when working with locally installed PC programs and storing all data records on a local hard drive is deceptive. This is because it is precisely when driver and vehicle-related data is stored, analysed and processed within seemingly closed local IT infrastructures that it is potentially exposed to a higher risk. This may sound paradoxical, but in view of the attack vectors mentioned above (possible ways of unauthorised access), such ‘classic office scenarios’ offer a multitude of possible gateways for criminal misuse. The sources of error are both man-made and technical in nature.
This is because a large part of day-to-day administrative business in the transport sector consists of collecting and exchanging information and data. The channels used for this are always potential starting points for cyber-attacks: Email inboxes, links on websites, a data CD-ROM, USB sticks or memory cards, even a phone call can allow attackers to gain unauthorised access to passwords, data or system functions. The tactics used to persuade users to make a fateful click, to use manipulated storage media or to pass on confidential information in a fictitious telephone call are just as sophisticated as the software that ultimately makes the hack technically possible. It is no coincidence that this part of deliberate user control is also known in specialist circles as ‘social engineering’.
It is often impossible to train all employees on the latest cyber threats and the tactics of potential attackers during day-to-day operations. Maintaining an overview of necessary software and hardware updates without calling in expensive external expertise also seems extremely difficult for many small to medium-sized companies. Caught in the dilemma between a core business that is demanding in terms of time and costs, and the dangers of the digital age, it therefore seems all too understandable when transport companies ultimately opt for the ostrich strategy.
To keep your finger on the pulse in this difficult situation, it is advisable to work with a suitable partner. This is because more modern solutions enable the encrypted transfer of data via the G network (remote download) to highly secure servers (mainframes for storing enormous amounts of data). This data can then be processed on multiple devices, regardless of location and number of devices. Access to and processing of the data is made possible via security barriers, such as strong password protection. A web platform replaces the user interface of a static, local programme for displaying and editing the data. In IT jargon, this is referred to as a ‘cloud solution’.
In the world of transport, this means that employee and vehicle data, tachograph, driver card and vehicle data (FMS data) can be called up online at any time. The relevant information can therefore be accessed from any Internet-enabled device worldwide and by different users at the same time. It is also easy to set which employees can see and work with which data. The good news is that you do not need to invest in a new and extensive computer infrastructure (hardware) for a cloud solution.
What does this mean for those who use remote download for driver card and tachograph data and the DAKO cloud solution?